Effective management of firewalls plays a crucial role in ensuring network security. Check Point Firewall is a powerful and flexible solution for this purpose. In this article, I will explain how to add a network feed in Check Point Firewall step by step. I will indicate where you can insert […]
Network
A computer network is a set of computers sharing resources located on or provided by network nodes. Computers use common communication protocols over digital interconnections to communicate with each other. These interconnections are made up of telecommunication network technologies based on physically wired, optical, and wireless radio-frequency methods that may be arranged in a variety of network topologies.
This script assumes you have the necessary permissions to access the Checkpoint local logs directory and upload files to the FTP server. Make sure to replace the placeholder values in the script with your actual FTP server information, username, password, local logs directory, and FTP logs directory. If you are […]
Cisco switches are essential networking devices that provide connectivity between different devices on a network. They come in different sizes and configurations to meet the varying needs of different organizations. In this blog post, we will discuss the initial configuration of Cisco switches to get them up and running. Before […]
Network monitoring is the process of observing and analyzing the performance and availability of a computer network. Network monitoring can help identify and troubleshoot network problems, optimize network performance, and ensure network security. Network monitoring can be done using various tools and techniques, such as: Ping A ping is a […]
Checkpoint is a leading provider of network security solutions that protect organizations from cyberattacks and threats. One of the key features of Checkpoint products is the three-tier architecture, which consists of three components: Smart Console The SmartConsole is the component that provides a graphical user interface for the administrators to […]
This configuration document was created by muscal for configzone. If you want to configure 802.1X authentication on a Huawei switch, you need to follow these steps: Set the NAC mode to unified by running the command authentication unified-mode. The switch will restart after this command. First of all, you need […]
Network security is necessary to prevent unauthorized and unauthorized access to your network, prevent data breaches and protect it from possible cyber threats. While ensuring network security, controls are implemented using various hardware and software solutions at different points within the network. In addition, processes, rules and configurations related to […]
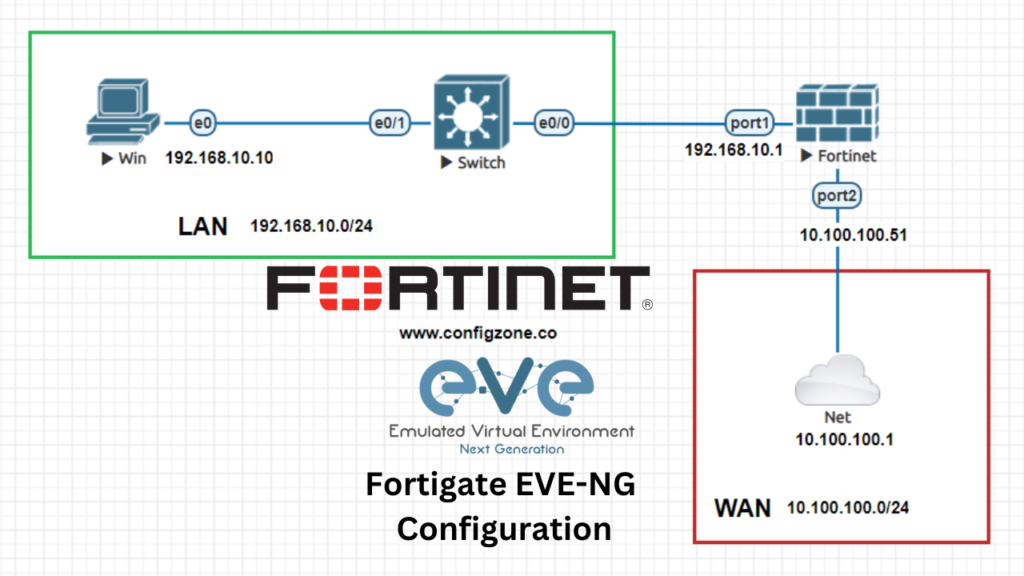
In this blog, we will add Fortigate in a topology we created on Eve-NG. Then we will add a windows 7 and connect the windows7 machine to the internet. First of all, you need to look at the topology below. I briefly explain the above aggregation. There is a 192.168.10.0./24 […]