Table of Contents
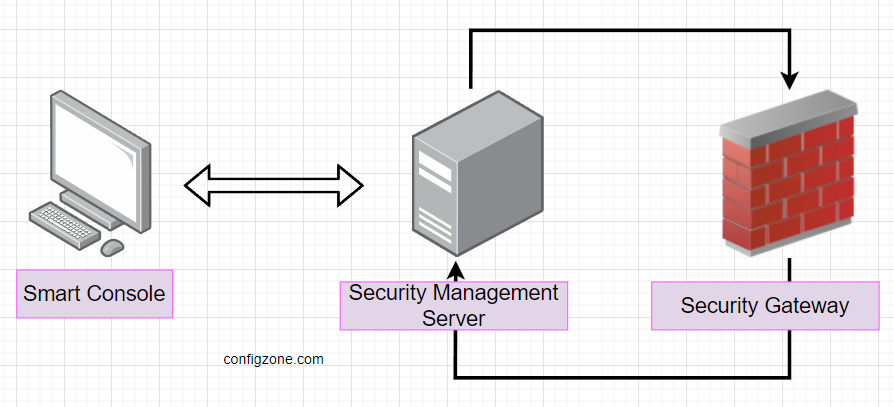
Checkpoint is a leading provider of network security solutions that protect organizations from cyberattacks and threats. One of the key features of Checkpoint products is the three-tier architecture, which consists of three components:
- Smart Console
- Security management
- Security gateway
Smart Console
The SmartConsole is the component that provides a graphical user interface for the administrators to manage and monitor the network security. It connects to the management server and allows the administrators to create and edit security policies, view logs and events, generate reports and alerts, and troubleshoot issues. The SmartConsole can be installed on any Windows-based computer.
Smart console provides a graphical interface for centralized management of the check point environment.
Create and Manage
- Security polices
- User and administrator accounts
- Management Servers, Gateways and devices
- Setting for check point environment
Monitor
- Logs and event
- Performance
- Regulation compliance
Maintain:
- License
- Update products
SmartConsole İnterfaces
- Desktop Clients (Windows host)
- SmartConsole Client
- Portable SmartConsole (R81.10 and higher)
- Clientless, Browser-Based interface
- Web SmartConsole (No installation package) : https://<management server ip>/smartconsole
Not: Installation package (Exe file) for SmartConsole Client and Portable SmartConsole are available from these locations.
- Check Point Quantum R81.20 Hom Page
- Check Point Support Center
- Gaia Portal
- Security Management Server
Smart Console Main Windows
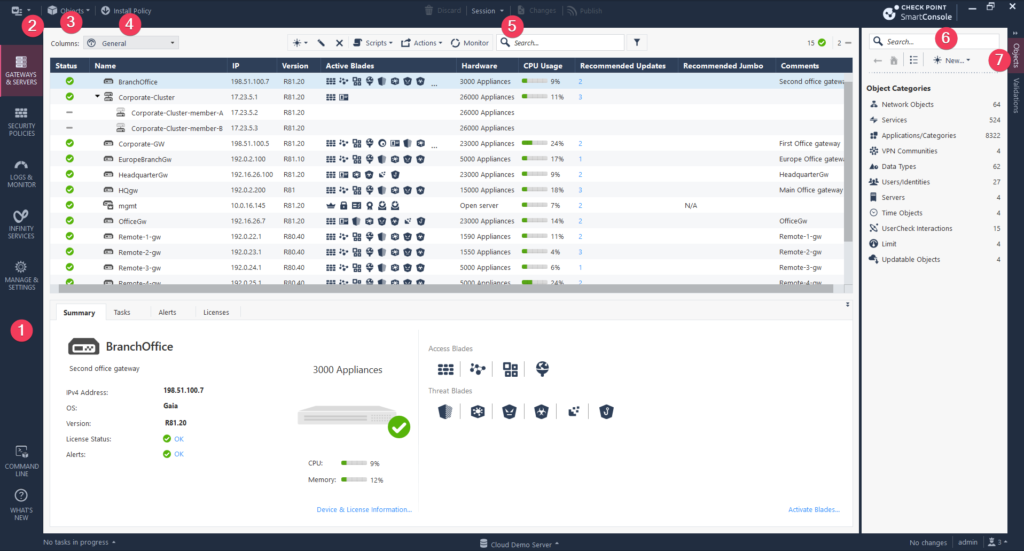
- SmartConsole Navigation Toolbar
- Gateways and Servers
- Security Polices
- Log and Monitor
- Infinity Services
- Manage and Settings
- Command Line
- What is NEW
- SmartConsole Application Drop-Down Menu
- Objects Drop-Down Menu
- Install Policy
- Session Management Controls
- Discard
- Session
- Changes
- Publish
- Search Box
- Object and Validation Bar
Management Server
The management server is the central component that manages and configures all the security policies and settings for the network. It also collects and analyzes logs and events from the security gateways and provides reports and alerts. The management server can be installed on a dedicated appliance or on a general-purpose server.
There are two Security Management options: Check Point Quantum Smart-1 appliance and open servers.
The Management Server is responsible for these roles and functions
- Database
- Internal Certificate Authority (ICA)
- Log Server
- Licenses and Contracts Rpository
- Monitoring
- Security Automation
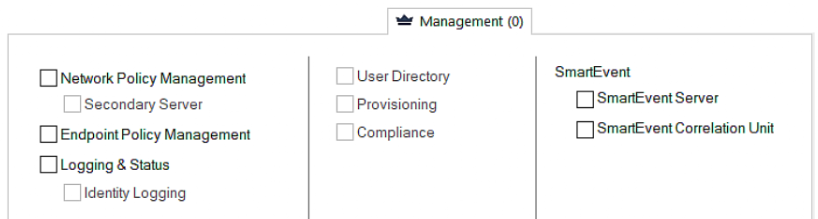
Security Management Server Software Blades
- Network Policy Management
- Endpoint Policy Management
- Logging and Status
- User Directory
- Provisioning
- Compliance
- SmartEvent
The features are organized in smart console. You can see bellow in the figure. For more information about features and blades visit to Check Point page.
Security Gateway (Check Point Firewall)
The security gateway is the component that enforces the security policies and rules on the network traffic. It inspects and filters packets based on various criteria, such as source, destination, protocol, port, application, content, and user identity. The security gateway can also perform advanced functions, such as VPN, firewall, intrusion prevention, anti-virus, anti-spam, and web filtering. The security gateway can be installed on a dedicated appliance or on a general-purpose server.
Check Point brochure link is here:
Check Point Security Gateway (Firewall) are designed all types and size;
- Hyperscale Network Security
- Data Center
- Large Enterprise
- Midsize Enterprise
- Branch Office
- Small Business
- Industrial Appliances
Security Gateway Blades
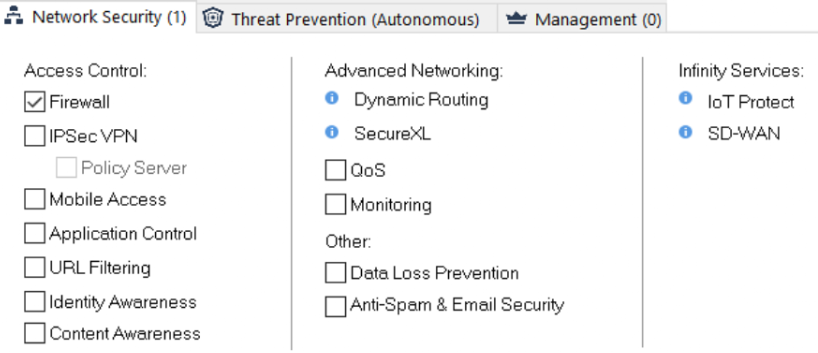
Threat Prevention Features and Blades
Two main types of Gateway Blades: Network security and Threat Prevention. Blades are enabled or disabled as required.
Threat Prevention features for gateways include the following:
- Sandlbast Threat Emulation, Threat Exraction and Zero Fishing
- IPS
- Anti-Bot
- Anti-Virus
Deployment Scenarios
There are two deployment scenarios: Standalone and Distributed.
Standalone Deployment
This deployment mode the Security Gateway and Security Management Server are installed on the same computer or appliance.
Distributed Deployment
Distributed Deployment the Security Gateway and Security Management Server are installed on different server or appliance.
